The Dynamic Host Configuration Protocol (DHCP) can automate the configuration of new systems added to networks and improve the management of existing systems on networks using Internet Protocol version 4 (IPv4) and IPv6. Deploying and configuring DHCP for IPv6 (DHCPv6) is one way to assign addresses on an IPv6-enabled network. Stateless Address Autoconfiguration (SLAAC) is another way to assign addresses on an IPv6-enabled network.
DHCPv6 is not just the familiar DHCP for IPv4 (DHCPv4) transliterated into IPv6 – and you need to understand the differences before planning for and deploying DHCPv6. This article explains those differences at length. This article offers historical background describing some of the differences between DHCPv6 and DHCPv4, and how DHCPv6 and SLAAC changed network administration.
DHCPv6 comes in 2 flavors: stateless DHCPv6 (originally called DHCPv6 Lite) which uses SLAAC, and stateful DHCPv6 which does not. This presentation can help you decide whether you really need DHCPv6 on your network. (It is not a given.) This article explores the differences between DHCPv4 and stateful DHCPv6.
This article includes a table that provides a quick review of the DHCPv6 and SLAAC options that various operating system manufacturers support.
This article is organized into 5 parts:
- Review of basic functionality and terminology for DHCPv6
- Review of basic functionality and terminology for SLAAC
- Configuration examples for different DHCPv6 clients, servers, and relay agents
- Definition and prevention of rogue Router Advertisements (RAs)
- Reference documents for DHCPv6.
1. Review of basic functionality and terminology for DHCPv6
This paper by Benjamin Long at the University of New Hampshire InterOperability Laboratory was written in 2009. It provides a basic overview of DHCPv6 configurations, Domain Name Server (DNS), and Session Interface Protocol (SIP) concepts, defines relevant terminology, and discusses issues to consider when configuring DHCPv6 servers and relay agents, or when deploying cascading relay agents. This paper (part1 and part2) written in 2014 goes into more detail on the creation of client addresses on DHCPv6-enabled networks.
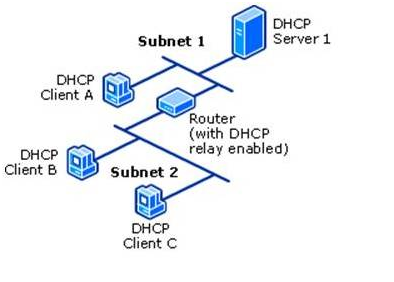
The DHCPv6 server is usually on a different link/subnet than most of its clients. On each link where the DHCPv6 server is not directly connected but clients are present, a router on the link must be configured as a relay agent. That router will typically be the one that also transmits RAs for that link as described by Internet Engineering Task Force (IETF) Request for Comments (RFC) 8106. Depending on the network topology, a series of cascading relay agents (either routers or computers) are configured on the intermediate links between the DHCPv6 server’s link and the clients’ links.
Note: A 2022 tutorial on the many aspects of DHCPv6 can be found in this All Things TECH IPv6 DHCP (DHCPv6) Server & Client Explained article.
2. Review of basic functionality and terminology for SLAAC
The article IPv6 Address Management – stateless, stateful, DHCP ... oh, my! discusses basic SLAAC, stateless DHCPv6 + SLAAC and stateful DHCPv6 addressing. Part 1 and part 2 of this article discusses SLAAC addressing in more detail. This article discusses two underlying features of IPv6 that enable SLAAC: Neighbor Discovery Protocol (NDP) and Internet Control Message Protocol (ICMP) for IPv6 (ICMPv6), while this article discusses Unique Local Addresses (ULA), and this article (and an update to it) discusses Extended Unique Identifier 64-bit (EUI-64) addressing. RFC 8981 discusses an extension to DHCP that enables hosts to generate temporary addresses with randomized interface identifiers.
Note: A 2022 tutorial on the many aspects of SLAAC can be found in this All Things TECH IPv6 Configuration, EUI-64, SLAAC & Dual Stack article and a tutorial on the many aspects of ICMPv6 can be found in this All Things TECH ICMPv6 and IPv6 Neighborships article.
3. Configuration examples for different DHCPv6 clients, servers, and relay agents
The National Institute of Standards and Technology Special Publication 800-119, Guidelines for the Secure Deployment of IPv6, was written by Sheila Frankel, et al, in 2010. It covers a wide range of subjects about the IPv6 protocol. In particular, section 3.5.4 and sections 4.7 through 4.7.3 (inclusive) discuss selected DHCPv6 and SLAAC topics:
- Tradeoffs between use DHCPv6 and SLAAC
- RA flag configurations
- Exchanges of messages between DHCPv6 server and client
- Security ramifications of DHCPv6.
The Samenwerkende Universitaire Reken Faciliteiten Network (SURFNet) IPv6 Deployment In Local Area Networks was written by François Kooman in 2011. It discusses static, SLAAC, and DHCPv6 address assignment mechanisms in more detail than SP800-119. It also discusses static, Recursive DNS Server (RDNSS), and DHCPv6 DNS assignment mechanisms.
On the PennState IPv6 Home website, this page provides configuration examples or links to examples for several DHCPv6 servers, including Cisco IOS, Dibbler, ISC, Nominium, and Microsoft Windows. That same page also provides configuration examples or links to examples for a variety of clients, including AIX, FreeBSD, Apple macOS and OS X (w/ Dibbler), Red Hat, Solaris, Ubuntu, and Microsoft Windows (w/ and w/o Dibbler). On the Juniper website, this article provides a configuration example for a Juniper JUNOS DHCPv6 server. This list of articles provides configuration documentation for DHCPv6 on Cisco IOS.
The article Setting up DHCPv6 to Dynamically Issue IPv6 Addresses in a Network describes the configuration of a Windows 2008 R2 (and later) dual-stack DHCP (DHCPv6 in addition to legacy DHCPv4) server and its clients while another article describes the configuration of a Windows 2012 (and later) dual-stack DHCP server. Maintaining pre-assigned static IPv6 addresses for routers and other infrastructure elements (DHCP Reservations), and how to set up more than one DHCP server are also covered.
Relay agent configurations for Nokia routers are described in this article, for Extreme Networks NetIron routers in this article (page 397), for Cisco IOS routers in this article, for Juniper JUNOS routers in this article, for Linux computers using dhcp6r or rtadvd, and for Microsoft Windows computers in this article. Additional relay agent configurations for Cisco Control And Provisioning of Wireless Access Points (CAPWAP) Access Controller (DHCPv6 Option 52 per RFC 5417), DHCPv6 Client Link-Layer Address Option per RFC 6939, and DNS Search List (DNSSL) Option per RFC 8106 are described in this article .
4. Definition and Prevention of rogue Router Advertisements (RAs)
On every link, there should be only one relay agent transmitting RAs. Whether by accident or malice, RAs transmitted by any unauthorized relay agent are called rogue RAs. By usurping the role of the relay agent authorized to send out RAs, such rogue RAs cause confusion and misconfiguration of other systems on the link. Rogue RAs are described in more detail by RFC 6104. Various vendors are actively implementing RA Guard, described by RFC 6105, to make it easier to detect and block Rogue RAs. RFC 7113, an update to RFC 6105, suggests ways to mitigate attempts to circumvent RA Guard.
A frequent source of accidental rogue RAs is the addition of a Microsoft Windows system that has Internet Connection Sharing enabled to an existing network, as discussed in the Windows Internet Connection Sharing (ICS) article in the Security section. Additional causes of rogue RAs and approaches to dealing with them are described in Section 5.2 of Nippon Telegraph and Telephone (NTT) Information Sharing Platform Laboratories Deploying IPv6: Problems and Solutions.
This Cisco white paper provides an in-depth description of the situation and suggests ways to detect and prevent rogue RAs. On the PennState IPv6 Home website, the IPv6 Security web page describes general IPv6 security techniques. In particular, the RA filtering and Rogue DHCPv6 server sections of that web page provide RA filtering or blocking suggestions for Cisco, HP, Juniper, and 3Com routers. This article discusses disabling RAs on both routers and hosts.
5. Reference documents for DHCPv6
- Nokia OS
- Extreme Networks NetIron IPv6 Configuration (page 139)
- Cisco IOS Switch and DHCP Server
- Juniper JUNOS
- Oracle Solaris
